A Complete Guide to Man in The Middle Attack (MitM)
Our Cyber Security Consultant think that this information is a must at this time, especially that we are using the web most of the time
Introduction
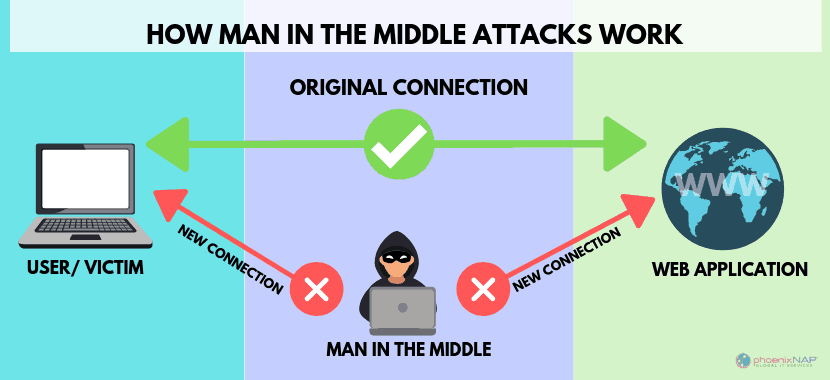
In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle (MITM) or person-in-the-middle (PITM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within the reception range of an unencrypted Wi-Fi access point could insert themselves as a man-in-the-middle.
What is a MITM attack?
An MITM attack is a form of eavesdropping, in which the attacker relays, corrupts, or alters the messages, either in transit or when arriving at the destination. The most common form of such an attack is the so-called Man in the Middle attack, in which an attacker intercepts communication in between two parties, intentionally or not. For example, a man-in-the-middle attacker is able to intercept network traffic sent from one target to another, usually the internet browsing traffic to a browser or a program or file being opened on the second target. To this end, the attacker must be in the same network as both targets. If the attacker is in the same network as the targets, they are able to cause an interconnection error.
Why does a MITM attack work?
In common online communication schemes, the attack can be effective because the attacker already has access to both parties’ public keys and their public keys are generally required to use encryption or verify signatures. In most cases, the attacker will not need to perform sophisticated data exfiltration because it is trivial for them to obtain sufficient access to one of the user’s e-mail accounts to steal the password. Because the attacker has prior access to the users’ keys, they can insert themselves as the server of the transactions and they can even hide the attacker’s connections from the victims. By creating intermediate servers, an attacker can have the victims believe that they are talking directly to the authentic party in a communication.
What is the difference between a MITM attack and a spoofing attack?
A spoofing attack can make an attacker appear to send a message to a victim even though he is communicating with an entirely different victim. For example, if a hacker gains access to the communications system of a popular online retailer, he can impersonate a legitimate user of the system. A targeted victim then connects to the attacker’s “real” account and logs in; when the account owner logs out, the victim is tricked into believing that they have logged out. The attacker now has access to a victim’s contact list and sends messages to their contacts pretending to be the targeted victim. For example, if a hacker sets up a fake Facebook account, he can post a message or pictures onto the victim’s account that they have posted, but in fact they never posted.
How does a MITM attack work?
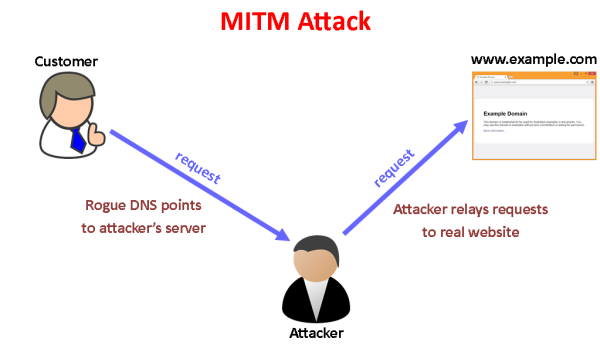
Man-in-the-middle attacks involve a malicious party creating an intermediate connection between two parties, allowing them to read and modify data transmitted by the victim while pretending to be the victim, thereby tricking the victim into believing they are communicating directly with each other. To do this, the attacker creates a hidden, pseudo-connection between their own computer and the victim’s computer. Once the connection is created, the attacker relays all data sent by the victim through their connection to the victim’s computer and replaces the original message from the victim with one that is modified by the attacker. How does the attack fail?
Common MITM attack scenarios
In these common cases, you are likely communicating with a partner that you know to be trusted, such as your bank or ISP. A simple man-in-the-middle attack makes it appear that you are talking to someone else, when in fact the attacker is intercepting all of the messages and has had full control of them for some time. This is often a condition of any service that uses HTTPS encryption for communications. In practice, this method of attack can be very successful. The attacker has an information advantage over the victim, who is only aware that the communication is happening, and is in fact reusing or not encrypting the messages. A different kind of man-in-the-middle attack is the peering attack, which is often used by ISPs to monitor and manage traffic.
Conclusion
Although PITM is a threat to ISPs and other corporate networks, there is little evidence that the attacks are anything more than hypothetical examples. Nevertheless, ISPs should be on the look-out for increased network traffic, and/or an increase in domain name server requests on their systems, especially as DNS servers are hosted in ISPs’ data centers. At the very least, ISPs can consider experimenting with SONET for additional point-to-point communication or implement dynamic host configuration to boost performance and/or increase security.
Follow us at other platforms.
Company Accounts:
LinkedIn: https://www.linkedin.com/company/13288994
Facebook: https://www.facebook.com/wallstreetconsultancy/
Twitter: https://twitter.com/Wallstreetuae
Instagram: https://www.instagram.com/wall_street_consultancy/
Quora: https://www.quora.com/profile/Muaiad-Al-Hariri-CPA
Pinterest: https://www.pinterest.com/MuaiadMAlhariri/_created/
Tumblr: Tumblr
YouTube: https://www.youtube.com/channel/UC_TbhAcktrIFAI_j5-6DElg?view_as=subscriber?sub_confirmation=1
Telegram Channel: https://t.me/Finance369
Udemy Latest Course: https://www.udemy.com/course/reading-financial-statement/?referralCode=44D4DFCEFFCA76BF3D5A
